What Are The Benefits Of A VPN Concentrator?
Virtualization innovation joined with the utilization of cloud-based organization edge arrangement gives numerous significant advantages, beginning with touchless, mechanized help sending and actuation. Regardless of whether virtualized and conveyed in the cloud or downloaded for the procedure on Bare Metal Virtual Customer Premise Equipment (vCPE), VPN concentrator switch limit and administration equality can be robotized and planned dependent on expected interest. By eliminating the constraints of a committed equipment gadget, virtualization innovation gives expanded dependability and higher organization accessibility.
VPN specialist co-ops can exploit utilizing Virtual Smartnode (VSN) VPN workers to convey a safe, encoded VPN administration to clients. Since it depends on NFV innovation, the number of clients and the nature of administration for every client can be effortlessly increased, downsized, checked, oversaw.
Edge Organization
Regardless of whether virtualized VPN programming is conveyed in the cloud or downloaded and introduced on an uncovered metal general CPE (UCPE) at a supporter’s premises, network edge organization (also known as Intelligent Edge) is normally executed, arranged, scaled (above) or beneath). ), checking and controlling VNF-based virtualized VPN programming administration and VPN network execution.
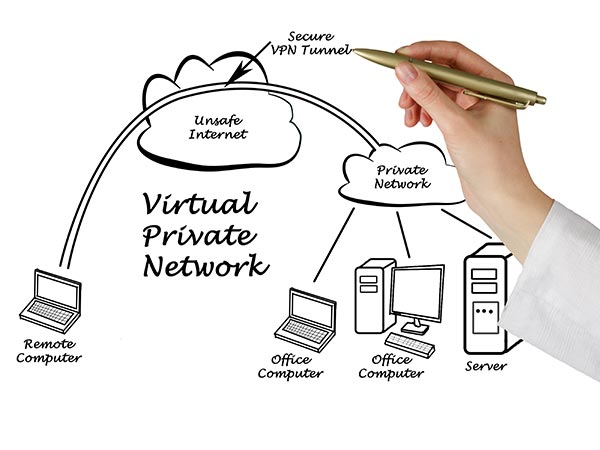
Prologue To VPN Concentrators
Security is a typical subject with regard to organizations with different geographic areas. As subjects like work from home have become more well known and presently the current climate is constraining organizations to telecommute, this issue has expanded. Be its clinical data, monetary data, or other exclusive data that is expected to go across network roadways, it is the undertaking of the present IT gatherings to safely get that information from guide A toward point B.
While virtual private organizations (VPNs) have existed for almost 25 years to scramble information for transport, as more clients and more information necessitate that encryption, VPN concentrators have had the option to deal with the progression of clients and information encryption for an association. are needed to do.
Vpn Concentrator
VPN connectors are once in a while alluded to as cutting-edge VPN switches. While the capacity of a VPN concentrator can be dealt with by programming, it relies upon the CPU’s capacity to deal with the heap as it is asset serious. The concentrator makes and oversees VPN burrows (or different passages inside an organization) in a unified way that will tie down information from the source to the objective.
This passage basically gives a protection plate covering the information as it moves to start with one objective then onto the next. They confirm clients, scramble, and decode information, just as determine IP addresses. This piece of equipment is set just external to the association’s framework and controls both the information and yield of data relegating a cryptographic key to every client.
VPN Concentrator will produce a safe passage with the goal that the client can get to any data moving through it. Numerous applications will produce this passage when the application is opened to safely ship the information. Without this security, an association opens itself up not exclusively to the capacity for unapproved people to get to the information, however to the capacity to embed malware into the information.
Related to know: what is a user id?
An unmistakable worth of VPN Concentrator is its capacity to deal with various clients. They can undoubtedly deal with 10,000 clients, regardless of where the clients are. Every client’s information is being scrambled all through the organization DB or framework permitting all-out security in the exchange interaction. Permitting this different piece of equipment to deal with this interaction ruins workers in enormous associations attempting to oversee and encode numerous surges of information.
Numerous VPN concentrators accompany solid firewalls notwithstanding encryption, the capacity to make burrows, and dole out passages to distant clients.
Huge Or Little Organizations
Positively, the size of the usefulness of VPN Concentrators makes them fundamental for huge associations with far-off workers. So the capacity to handily guarantee the security of information for 10,000 clients would cover numerous associations. In any case, what might be said about private companies? Private companies, regardless of whether lacking huge business financing, can and should exploit the advantages of VPN Concentrators, utilizing a solitary piece of equipment versus elective strategies.
There are standard Windows directing choices, which are conveying parcels of information from its unique source to the objective through the Microsoft Windows stage. There is likewise far-off access usefulness that a private company can use to get to their association from home. The issue with these techniques is that it leaves the space regulator, which is charged for validating clients, open to the Internet.
This represents a security hazard in the event that somebody runs over the IP address and the secret word Or attempts to accomplish the least security. This can spell catastrophe for an independent venture, however, fortunately, the choices for VPN Concentrator are immense. VPN concentrators are anyway more costly than VPN programs, so it may not be the most ideal alternative for an independent venture, and surely isn’t required for home organizations.
What Are Vpn Concentrator Alternatives?
There are numerous choices accessible which rely upon the requirements of the clients. for instance:
- Are clients working from their homes?
- Do clients consistently live in various areas, like a mobile sales rep?
- Is it accurate to say that they are in a structure where IPsec is obstructed from going through a firewall like numerous areas of interest are set up to act?
- Is adaptability required?
- Should the information additionally be adjusted with an outsider?
Vpn Concentrator Alternatives
There are a few different ways to convey usefulness like VPN Concentrator, contingent upon your organization’s requirements. How about we take a gander at a portion of these.
Vpn Switch
Some VPN switches can burrow, however, consider what sort of uses you’ll use just as what sort of access you’ll require. These might be more affordable, yet are worked to be more adaptable and strong than VPN concentrator switches. The switch requires the customer’s far-off gadget to be arranged in an unexpected way. The expense can rapidly offset the advantages with this choice, contingent upon the number of workers.
Site-to-site Vpn
This alternative is generally important if by some stroke of good luck a few locales should be associated without a moment’s delay and you don’t have to manage other distant associations. Anyway, burrowing conventions are set up at explicit information bases and areas. VPN Concentrators are a superior choice if distant access is required.
Far Off Work Area Programming
These likewise make a protected association between the source and the organization. These associations will be designated either inside the authoritative office or on an incredibly limited scale. It’s anything but a substitute for medium to huge associations to deal with far-off access.










